The Dark Web Exposed Part 2
Welcome Back
Last month, we started our unfiltered dive into the dark web by explaining the basics. If you missed Part 1 you can now access it on our website.
Before we start, we want to reiterate that playing around on the dark web can have serious repercussions. Given its daunting and enigmatic reputation, most people have never ventured out to see what really exists on the dark web. We'll give you a peek behind the curtain so that you don't have to put yourself at risk!
SEVN-X does not endorse or condone any material or activities mentioned in this article, nor does it seek to provide commentary or regard with bias any of the sites, users, or material depicted. Screenshots are included for educational purposes only.
Are You Afraid of the Dark?
First things first, we must download and install the Tor browser. Because we can never be certain about what lurks out there, we set up throwaway Windows VMs in Amazon when doing research, investigations, and for this exploration. We highly discourage accessing the dark web on a device that contains any sensitive information.
Once we have installed Tor, we will take a look at some of the settings to make sure we are operating in the most secure manner possible. Again, these sites are unfamiliar to us and there is no way to know if the site will attempt to take malicious action(s). For starters, we enable an extension that will block scripts from running automatically, which could protect us from malicious redirects or drive-by downloads.
It is now time to start looking for web sites. But how do we find them? ...
Unlike the surface web, sites on the dark web do not have normal, human-readable domain names – such as example.com. Instead, dark web domain names are comprised of a random string of letters and numbers—and these change frequently. Another notable feature is that every web address ends with the .onion suffix instead of the standard .com, .org, etc. TLDs.
We will try to locate a web resource known as a hidden wiki. Hidden wikis are sites that provide a directory listing to all kinds of websites, conveniently organized by category. Once we find a hidden wiki, we have quick and easy access to links for all kinds of web sites. The .onion address for a hidden wiki can actually be found on the surface web; after a quick search, we found a valid URL for a hidden wiki.
From here, we can also find specialized dark web search engines. Although not as robust, these search engines can still be quite helpful for finding sites not listed on hidden wikis.
With a plethora of URLs at our disposable, we can begin exploring...
What is Out There?
Most people think that the dark web is just for crime and drugs. While that may be true, there are other "crimes" on the dark web that we may not immediately recognize as criminal. Take freedom of speech for example. It's not an inalienable right in every country.
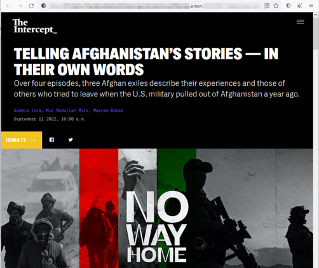
So for our first stop, we'll visit a journalism site. Here can be found an Afghani documentary detailing the experiences of exiles and their adverse journeys in a time of upheaval. Perhaps this piece had to become available to the world through the dark web as a way of avoiding censorship and individual persecution.
Controversial Investigative Journalism
Virus Maker?
Next on a general IT/security interest site, we found a program that generates customized computer virus executables. Based on the nature of the site and a related disclaimer, it seems like this is disseminated for educational and research purposes. However, one can imagine how this might be used in the wrong hands.
Virus Executable
Some parts of the dark web attract users for perfectly innocuous activity. Below is a forum populated with threads discussing various art subjects.
Now that you've seen how some of these applications, join us next month for Part 3 of our Dark Web Exposed series where things take a more sinister turn...